
If you want to know more or are interested in collaborating with us on any of our research, please contact us at hiai@fit.edu or call us at +1 (321) 674 8590
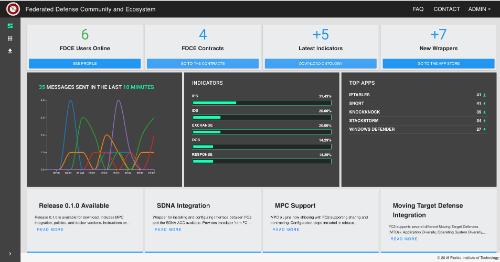
FDCE is an open environment where organizations choose to join and participate on a collective defense through the automatic and contextualized sharing of information and coordination of responses, thereby alleviating the difficulties and time delays associated with manual information sharing between organizations.
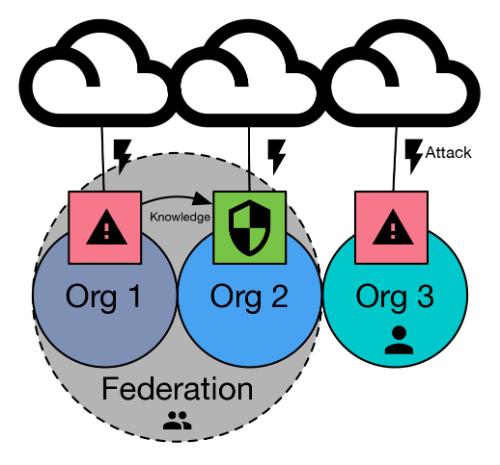
The interdependence between organizationally independent computer systems is pervasive throughout government, industry, and the private sector. While independently managed and operated, these systems depend on each other for the functions necessary to conduct business and achieve organizational goals. With the increasing transition of enterprise to operate over private (or shared) cloud infrastructures, the boundaries of enterprises become less clear, and there is a greater need to enable security across organizations. In an effort to develop tools, techniques, and architectures to enable smarter information and defensive posture sharing, DHS S&T has funded the development of a Federated Command and Control (FC2) framework for cyber defense operations. The FC2 effort has demonstrated how multiple organizations can easily and dynamically come together and operate through a policy-controlled federated infrastructure to contextually share interests, indicators, defenses, experience, and playbooks that enable not only better individual defensive capabilities for each organization, but also a greater collective defense posture for the federation. The benefits of Federated Defense could be greatly enhanced by the establishment of a community of federation members and the development of a support infrastructure for real-time sharing of threat information, indicators, and recommended responses for all community members.
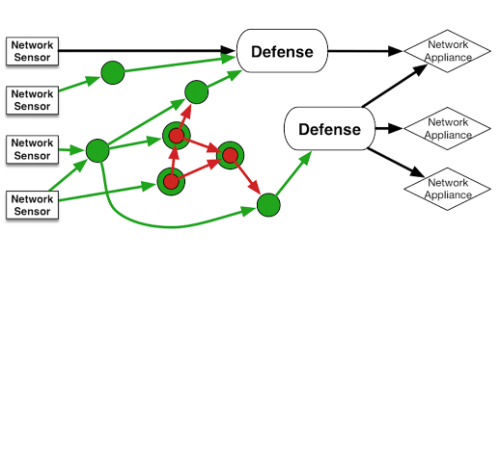
Federated Command and Control is a tool that increases the security of network infrastructures by sharing learned knowledge of attacks and defensive postures within federation.
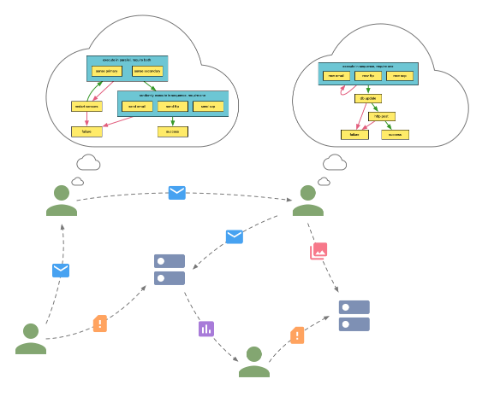
A realistic user modeling service that helps researchers study how the presence of cyber attacks and defenses affect an individual's ability to complete his/her mission.
A cyber operation scenario that replicates the conditions in a real world organization in terms of infrastructure, topography, network traffic, defenses and attacks in order to better understand the impact on scenario missions when an organization comes under attack.
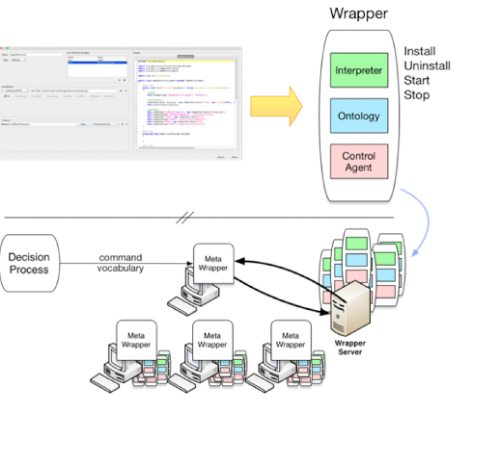
A system for semi-automated modeling, representation, and integration of moving targets defenses (MTD) into command and control infrastructures.
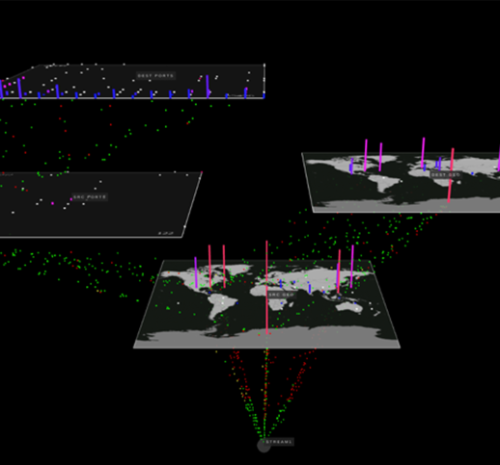
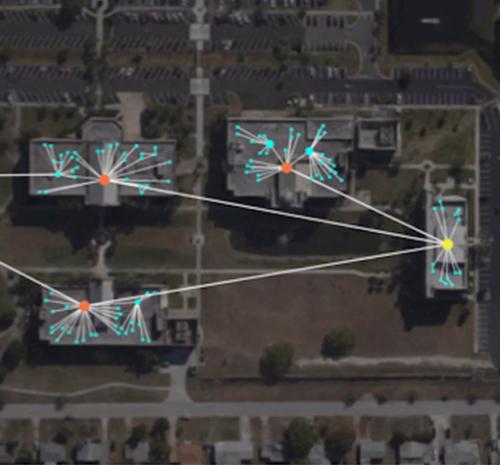
Building visual structures that enable network security operators to determine what behaviors are taking place on the network.
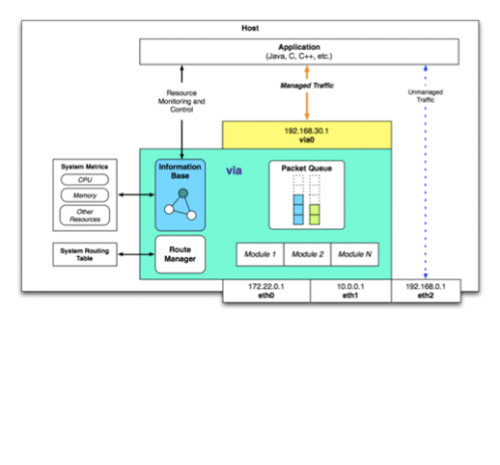
A cross-layer framework that enables applications to better adapt to dynamic communications environments by leveraging the underlying network infrastructure to support QoS requirements and constraints.
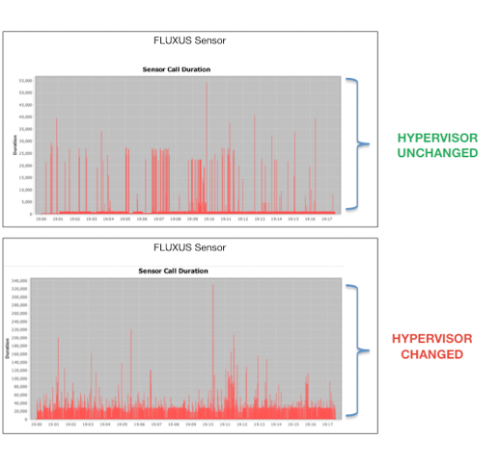
Fluxus is a sensor that detects changes in its execution environment based on timing analysis of system calls.
Research on resilient communication protocols for airborne networks at the transport and network levels, as well as integrated support of resilience at multiple layers in the system.
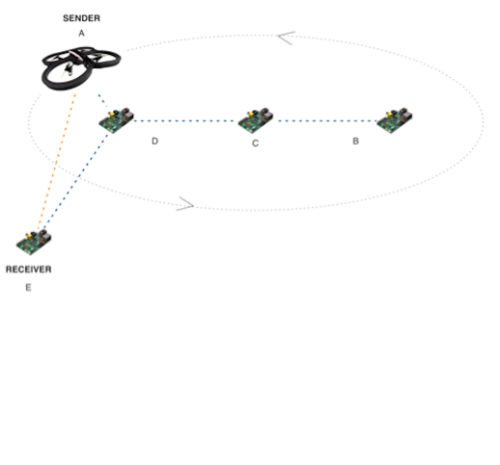
A control framework for software-defined radios to support MANET and cognitive network applications, using Universal Software Radio Peripherals (USRP) and small factor, single-board computers such as Banana Pi, Intel NUC and MinnowBoard.

Emulation systems that support different research tasks in the areas of network communications, distributed coordination and task allocation, path finding, collision avoidance, and optimization.
A Defense Quantification Service that takes defense implementations and metadata as inputs, and produces characterization profiles of the defenses for use as part of an integrated C2PD decision tool.

Research for a prototype agent-based infrastructure for pilot behavioral modeling in autonomous airborne vehicles.
Transitioning HIAI Cybersecurity research into tools and products that can be used by FIT network operators
© Florida Institute of Technology, All Rights Reserved